By | Kamarul Baharin bin Khalid, Muhammad Edwin bin Ambo Rifai, Ahmad Aizuddin Aizat bin Tajul Arif
Malware attacks are progressively becoming a real threat on Android devices. Malware or any potentially harmful application (PHA) labelled by Google has been haunting Android users for quite some time now. While most PHAs are not harmful, some do have the malicious intentions of abusing permission or worse, stealing a user’s data, especially online banking-related credentials or two-factor authentications (2FA).
This becomes increasingly dangerous for victims with rooted devices as it provides a leeway for the hackers to install a more malicious code that carries the ability to control the victim’s device. Figure 1 shows an increasing number of users who have been attacked by stalker were.
Victims with rooted devices are exposed to even higher risks as they are more vulnerable to malicious features including the ability to control a victim’s device.
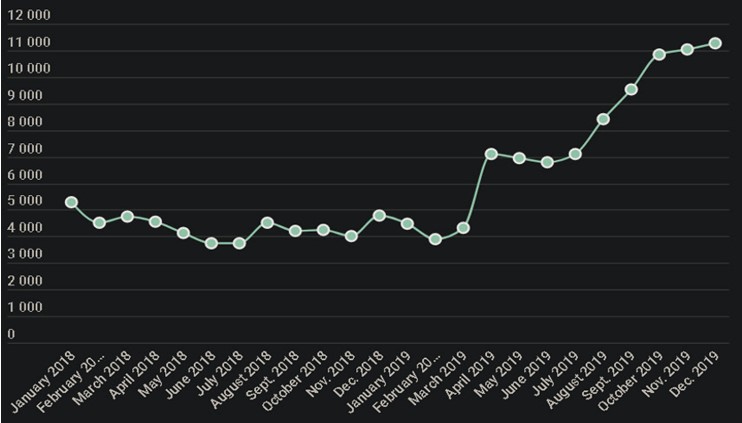
Figure 1: Number of unique users attacked by Stalkerware in 2018–2019
(Source: https://securelist.com/mobile-malware- evolution-2019/96280/)
Types Of Potentially Harmful Application (PHA)
Google has categorized these PHA based on motives, functionalities, and damages caused by malware once it has penetrated a user’s device. The categories are as follows:
- Backdoor: Allows the execution of unwanted, potentially harmful, remote-controlled operations on a device.
- Billing fraud: Automatically charges the user in an intentionally deceptive manner.
- Commercial spyware: Transmits personal information from the device without any notice or consent and it does not display any notifications regarding this occurrence.
- Denial of service: Executes, without the knowledge of the user, a denial-of-service (DoS) attack or is a part of distributed DoS attack against other systems and resources.
- Hostile downloaders: While it is not harmful on its own, but hostile downloaders bring other PHAs into a user’s device.
- Non-Android threat: This does not cause much harm to the Android user or device but contains components that are potentially harmful to other platforms.
- Phishing: Pretends to come from a trustworthy source, which requests for user's authentication credentials or billing information, and then sends the data to a third party.
- Elevated privilege abuse: Compromises the integrity of a system by breaking the application’s sandbox, gaining elevated privileges, or changing or disabling access to core security-related functions.
- Ransomware: Takes partial or extensive control of a device or data on a device and demands that the user makes a payment or performs an action to release control.
- Rooting: Roots a device and executes other actions that apply to other PHA categories.
- Spam: Sends unsolicited messages to the user's contacts or uses the device as an email spam relay.
- Spyware: Transmits personal data off the device without notifying and getting consent from the user.
- Trojan: Appears to be benign, but it performs malicious actions against the user.
- Uncommon: Classified as uncommon if Google Play Protect does not have enough information to clear them as safe.
Due to increasing malware threats on Android devices lately, it is highly recommended to only install applications from Google Play Store and only download trusted applications. Downloading applications illegally or from an untrusted source remains the primary means for the distribution of PHAs.

Why Trusted Sources
While Google Play Store may not be perfect, it is still the safest and trusted available means of application installation platform for the Android ecosystem. Other mobile phone manufacturers may also have their own trusted app store. So why trusted sources?
1. Applications hosted and checked by the Google security team
Google has teamed up with other security companies to help identify malicious applications before they are published on the Play Store to avoid potential harm to Android users. All Android applications must undergo rigorous security testing before it can be published on Google Play Store. Google goes to the extent of screening every application developer and does not hesitate to suspend those who violate their policies.
2. Google removes any app found suspicious
Google Play Protect is a software created by Google to automatically scan various applications every day in order to remove any suspicious applications. While there is certainly room for improvement, Google is constantly learning and improving its protection software.
What Is Google Play Protect?
Google Play Protect is a malware protection service developed by Google and deployed on the Google Play Store. It is also made available on every Android device by default. This is to protect Android users from downloading malicious applications.
Anti-malware by Google
This is one of the services provided by Google Play Protect to verify the applications. This service scans devices every day for any known signature of PHA. A warning will then be displayed for the users to respond when Google Play Protect detects a violation of malware policy. This is to let the user know that a PHA has been found and prompts the user to remove the application before any malware infects their device. In cases where the PHA has no benefit to the users, Google Play Protect can remove the PHA from infected devices and block any future installs.
Integrated into Google Play Store
As mentioned earlier, Google Play Protect scans a vast number of applications every day. Through these daily scans, Google Play Protect is able to respond quickly to any detected threat and thus, reduces the user’s device from being infected. About 93% of PHAs are discovered by the on-device daily scan. To conserve data transmission, these daily scans only contact Google servers to request a verification when a suspected PHA is detected.
Google Play Protect works in the background and only needs user interaction when a PHA is detected. Users can check when their device was last scanned and view the list of scanned applications in the Google Play Protect section of their Google Play application.
SafetyNet Attestation API
For application developers, the SafetyNet Attestation API is very useful as this anti-abuse ATI allows application developers to check for any security threats in the Android devices on which their application is running. The API is used as a part of the application’s abuse detection system module that helps the developers determine if the device has any security issues. This application can help determine whether their servers are interacting with genuine and unmodified applications that are running on a trusted and unrooted Android device.
This is extremely important especially if the application is handling sensitive information that includes the user’s name, address, identification number, bank account number, or even dealing with payment methods.
Malware Infected Android App
Android phones can fall victim to malware, just as computers do. Malware creates glitches and slows down the user’s device, thus making it difficult to use the phone.
The good news is that all applications installed on Android devices need user consent before installation. The bad news is that not all users are security savvy enough to detect malware from normal applications.
Attackers will always try to infect android installers with malware and share the installer. They just need to deceive a user into installing the malware by:
- Infecting a legit Android app with malware. With this method, the users assume that they are installing or updating a legitimate application but it is unknown to the user that malware is also being installed in the background.
- Creating an interesting application and attaching it with malware. With this method, the attacker makes a trendy application that appears to be interesting in order to attract users to install it. Once it has been installed, the malware will then be installed in the background.
- Creating malware which will pop up as an application update. When the user reads the pop-up notification, they would assume that they are installing an update, rather than malware.
Due to its malicious behaviour, all malware cannot be hosted in Google Play Store. However, there are several ways that malware can directly infect Android devices;
- Installed from a third-party app store. Third-party app stores do not have any verification method to certify applications that are hosted on their server. Attackers can easily host their malware here.
- Installed from a direct link. Attackers can subscribe to any web hosting or cloud services to host the malware on the platform. The service providers do not verify any application that is hosted on their server which means that the attacker only needs to share the link of the malware with the victim.
- Installed from a shared installer. The attackers can share the malware installer files directly onto social networking or social media platforms. Not all service providers will verify shared application

Things To Look For And Precautions
- When purchasing a new Android smartphone, it is important to make sure that the Android operating system is the latest version. This will ensure users that their device is protected with the latest security update. To check if your device’s Android version is the latest. Follow the steps below:
- Open device’s Settings app.
- Go to About phone > Software Information
- The Android Version displayed will be the version used in the smartphone. The latest Android version is 10.
- Check if your device’s security is up to date. Follow the steps below:
- Open the device’s Settings app.
- Go to About phone > Security patch level
- The date displayed is when the last security update was released. Newer Android OS receives monthly security updates.
- When installing an application, look out for any suspicious permission requests. For example, there is no necessity for a calculator application to request Internet access which might be a malware installing pop-up. The figure below shows an example of unnecessary permission requests.
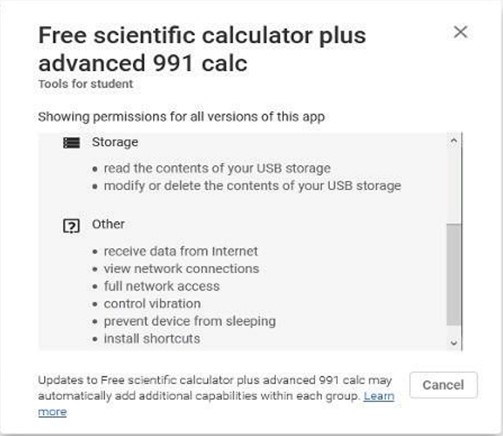
Figure 2: Example of Unnecessary Permission Request
- When installing an application update, an error pops up when trying to overwrite the originally installed application. This means that the new update installer is not the original installer but a modified installer that is not approved by the original developer certification.
- Only install applications from trusted source/App Store/Play Store. Do not install applications from a direct link or from a shared installer because a trusted source will vet all applications for malicious malware.
Recommendation
- Consider installing antivirus/anti-malware solutions that are offered in the Google Play store for extra protection.
- Install MASSA, an Android application by Malaysia Computer Emergency Team (MyCERT) or CyberSecurity Malaysia to automate the Android devices’ misconfigurations and risk identification. Reports that are generated by MASSA will be useful for a security analyst to help investigate any Android incident.
Conclusion
All Android devices with the Google Play store are installed with a set of endpoint and mobile threat prevention services that protect the device against common threats. It is always running in the background to protect the user’s device from malware and it has an automatic update with the latest bug fixes.
In general, Google Play Protect analyses all the applications that are newly installed and existing applications already on the user's device in order to check if any app contains threats.
- Keeping device safe, 24 x 7
- Securing a device even if it has been lost or stolen
- Scanning and verifying before installing an application
- Helping the users to navigate the Internet safety.





