By | Shaifullah Bin Mat Swadi
Cyber insurance is pivotal for the survival of digital dependent business operations. With the great reset of global reliance on online e-commerce platforms worldwide ever since the onset of Covid-19 pandemic, cyber insurance has become a necessity for companies to operate efficiently.
Based on Organisation for Economic Co-operation and Development (OECD), the cyber insurance market size in 2016 was estimated to be in the range of USD2.5 billion to USD 3.5 billion. The market size is projected to grow at around 20-25 percent annually, reaching USD20 billion in premiums by 2025 (Paul, Matthew , Matthew, & Arturs, 2017). Hence, it is imperative to ensure companies procure accurate cyber insurance premiums to protect against business operation exposure. Proposal questionnaire forms are the main assessment method for cyber insurance providers to evaluate companies’ cyber security posture. This is in accordance with findings by a study that self-assessment questionnaires presented client function in assessing their security posture (Sasha , Lillian, Andreas, & Therese, 2019).
Cyber insurance is pivotal for the survival of This paper compares questionnaires provided by AIG and Chubb to review the variety of data collection required by the companies. Briefly, both proposal forms (in line with the practices of most companies) employ self-assessments as part of the underwriting process (Rainer, Stefan, & Markus , 2019). This is to reduce uncertainties by An in-depth understanding on the questionnaires by the Malaysian cyber insurance companies is vital for the cybersecurity industry business’ ecosystem in supporting the pre and post cyber insurance procurement cycle. This paper dives in to review the list of questionnaires by two local insurance carriers on policy writing and premium price. Similar studies on proposal questionnaires based in UK and US by Woods et al (Woods, Agrafiotis, R.C Nurse, & Creese, 2017) provides an insight on what to look out for in the proposal forms provided by local cyber insurance companies.
Among the 22 licensed insurance companies and takaful operators sanctioned by Bank Negara Malaysia (Licensed Insurance Companies & Takaful Operators, 2021), only four companies offer cyber insurance. Table 1 depicts two companies that provide proposal forms via online: AIG Malaysia Insurance Berhad and Chubb Insurance Malaysia Berhad. Both proposal forms are available for download via public domain from https://www. aig.my/business/products/financial-lines/cyber- insurance and https://www.chubb.com/my-en/ business/cyber-insurance.html. considering the existing accumulation aspects and developing adequate pricing approaches (Dirk, Tino, & Johann, 2020). Review on this matter is vital because all parties involved in providing cyber insurance are interested in an efficient assessment process. Some clients tend to provide as little data as possible which poses a challenge. However, if too much data is requested, potential clients may choose a competitor. On the contrary, if too little data is requested, it may increase the risk to the insurers (Arnau, Ioannis, Louise, & Jason, 2020).
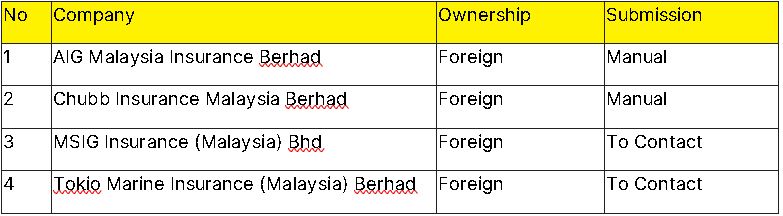
Table 1 Licensed Insurance Companies Offering Cyber Insurance
Findings
Table 2 reveals the spectrum of differences in terms of general and subtopic proposal questionnaires between AIG and Chubb. AIG questionnaires are straightforward with five main sections covering company information, data protection procedures, data access & recovery, outsourcing activities, and claims information. Briefly, the questions probe general practices and controls with regards to information security that the proposer (applicant) have in place. In the data protection procedures sections, key questions include data protection policy availability, compliance (staff), compliance (legislation), policy review cycle and availability of dedicated responsible staff in this domain which falls under process category.
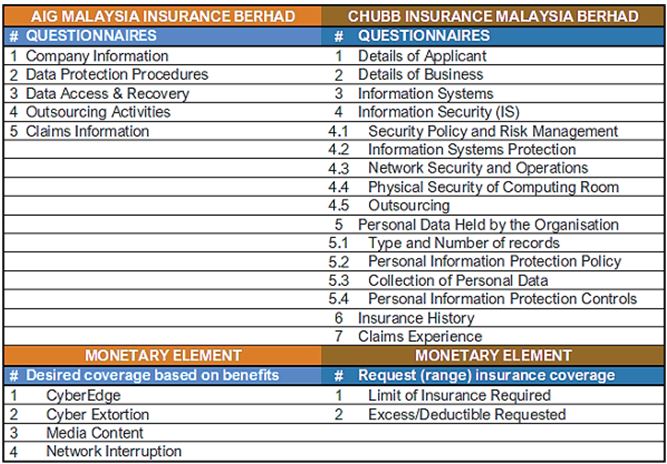
Table 2 List of Proposal Questionnaires
Chubb questionnaire covers detailed probing with majority through a yes or no answer option with a combination of small numbers of qualitative objective answer scheme. The main sections are details of applicant, details of business, information systems, information security (IS), personal data held by the organisation, insurance history and claims experience. In In data access & recovery section, the inquiry covers more on technological implementation in preventing unauthorized access from external networks and computer systems within internal networks. The questions also found on type of tools, equipment, controls, ecommerce modules, encryptions requirements, backup, and recovery procedures. Remote user authentication is also covered in the list of queries. In the outsourcing activities section, the questions focus outsourcing of network, computer systems or information security of the company processes, indemnification, compliances, and equipment. Lastly, the claims information section touches on company history (if any) with regards to investigation or audit in relation to data protection by a data protection authority and other relevant issues.
In the Information Security (IS) section, there are five* subcategories, which are security policy and risk management, information systems protection, network security and operations and physical security of computing room.
While in the personal data held by the organisation section, it is subdivided into four subcategories, namely type and number of records, personal information protection policy, collection of personal data and personal information protection controls. In the details of business section, the question is specific to the business operations with probing question on e-commerce activities if any. Among the highlighted question is the outage period before the adverse impact on the company’s business. Such question provides valuable input for assessment in policy writing and premium pricing. In the information systems section, the proposer must provide the number of end points and website service with e-commerce elements (if any) together with the revenue share from e-commerce.

Majority of proposal questionnaires reside in the information security (IS) and personal data held by the organisation section. In the information security (IS) section which consists of five subcategories, the list of questionnaires consists of policy, processes, audits, staff trainings, risk management availability, information system protection and network security as well as operations technologies. The yes or no options provide an easy quantitative assessment to produce the required result for premium pricing. This section also covers physical security of computing room capability with active/passive architecture and consists of details of outsourcing operation that also covers Service Level Agreements (SLA) for incident and change control and penalties in case of noncompliance with the SLA. Details of asset and service that is outsourced with a yes or no option together with objective answer options provides a thorough landscape of the outsourcing philosophy. The personal data held by the organisation section is subdivided into four subcategories covering complete probing of the viewpoint of how the proposer or applicant company manages personal data.
But what really differentiates this section is a question on the number of records that need to be insured which is further subdivided into six main region and categories/property of personal data that consists of commercial, financial and health data segmentation. In the following sections, the questionnaire covers personal information protection policy subsection which comprises policy formalization, awareness training, confidentiality agreement, monitoring, audit, and data breach response plan. The questionnaires focus on understanding the type of sensitive or confidential information that an applicant collects, stores and processes. While in the insurance history section, the probe is quite simple with enquiry on whether proposer has similar insurance along with details and status of coverage. Lastly, the claims experience section traces the company history (if any) with regards to lawsuits or any potential claim and relevant disciplinary action or investigation by any authority.
Conclusion
AIG and Chubb questionnaires portray substantially different approach in data collection. Simplicity seems to be the overall approach for AIG questionnaires, while Chubb chose a more rigorous regime. Despite the differences, the questionnaires seem to provide one common purpose, which is to provide insight into the security technologies and management practices (Sasha , Lillian, Andreas, & Therese, 2019). One similarity is request for required monetary coverage by the clients with direct coverage option for AIG. In Chubb’s case, the coverage is very objective and customised. The extreme difference seen from data collected through the questionnaires were also reviewed by James Sullivan and Jason R C Nurse; in which they highlighted that one area that requires further examination which is the varying approaches that these cyber insurers take to assess cyber risk within organisations. While some may take a high-level strategic approach to risk management (such as audits or questionnaires), including the use of a variety of cyber risk-management frameworks, other cyber insurers may take a more technical deep dive into the risk held within an organisation (James & Jason, 2020). These extreme varieties in questionnaires also conform to the findings by a report done by the European Insurance and Occupational Pensions Authority. According to the report, one widely recognised difficulty for the cyber industry is the lack of commonality in risk assessment language, which becomes evident in various aspects from coverage to underwriting questionnaires (Understanding Cyber Insurance A Structured Dialogue with Insurance Companies, 2018). Moving forward, it is crucial to have a standard guideline on the minimum threshold for cyber insurance proposal questionnaires to cover the three main cybersecurity elements: people, technology, and process. This is to enable cyber insurance solutions to stay dynamic in the industries. There must also be systems in place to capture data and design platforms where data can be easily searched and analysed (Arnau, Ioannis, Louise, & Jason, 2020) to compensate for extreme variation in questionnaires between cyber insurance providers. Other related potential research is how to balance between acquiring data from clients and securing cyber insurance business in the context of risk assessment that allows visualisation of the probability of occurrence and extent of damages due to cyber risks (Dirk, Tino, & Johann, 2020) in pricing the cyber insurance premium accurately.





