By | Muhammad Azri Rafiuddin bin Basri, Imran bin Hasnan & Lukman Hakim bin Abd Rahman.
Introduction
Developing a viable cyber security monitoring practice has been a challenge. As attack surfaces become more complex, every organization needs to be more vigilant. However, the development of new technologies and software has definitely made cyber security monitoring much easier. A successful security monitoring work can be accelerated by utilizing the new purple team exercises. Organizations need a viable security monitoring practice that can be utilized for procedures and processes that are sustainable.
Purple teaming is a security methodology in which red and blue teams work closely together to boost cyber capabilities through continuous feedback and knowledge transfer. One of the foremost successful ways to find framework vulnerabilities and foil conceivable cyber threats is through the skills and expertise of both red teams and blue teams.
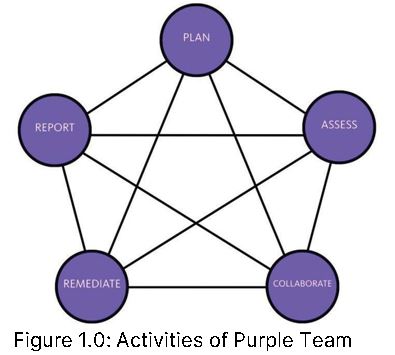
What is Purple Team?
Purple team is developed to help the security teams track the progress, viability and effectiveness of vulnerability detection, threat hunting and network monitoring by accurately simulating common threat scenarios of unused procedures that are outlined in order to anticipate and distinguish modern threats. Some organizations perform purple team exercises as a one-off focus engagement, whereby security goals, timelines, and key deliverables are clearly defined by the security team, with a formal process in evaluating lessons learned over the course of an operation. This practice includes recognising offensive and defensive shortcomings, outlining future training and technological requirements. An alternative approach within the security industry is to view purple teaming as a conceptual framework that runs throughout an organisation.
What are Red, Blue, And Purple Team?
A red team exists to attack, while the blue is to defend. The purpose is to fortify an organisation's security by learning from the resulting combat and getting ready when the real threat comes. A purple team is set up as an option to support the process. The red and blue team exercises can be extremely useful because it creates an opportunity to realistically challenge an organisation's defences.

Red Team
The red team is typically the independent security system of a company (target), and it is hired to covertly test its defences. The team comprises skilled ethical hackers whose objective is to distinguish and securely exploit vulnerabilities within the target's cybersecurity or physical perimeters. By mimicking sophisticated realworld threats, the exercise is highly realistic. A red team deploys bleeding-edge hacking tools and techniques designed to infiltrate the security systems and premises. This may expand to include writing malware and formulating modern techniques as noxious malicious hackers would do. Some organisations will be confident that their systems are hard to penetrate as they have a variety of vigorous security measures in place. But a red team only needs to find a weak link to break their perimeters apart. This could include spear-phishing (social engineering) the employees or replicating the target's external services in a lab to discover zero-day exploits.
The red team objectives include:
- Compromising the target's security by extricating data, invading its frameworks or breaching its physical perimeters.
- Dodging detection by the blue team. Numerous attacks can occur over a transitory period of time, making it highly dubious for the blue team to neutralise any threat before the 'damage' is done.
- Exploiting bugs and weaknesses in the target's infrastructure. This highlights any gaps in the organisation's technical security that requires fixing, thus improving its security posture.
- Starting a hostile action - including sophisticated penetration testing - giving a reliable assessment of the blue team's defensive capabilities.
Blue Team
A blue team is typically stationed within a Security Operations Centre (SOC). The SOC consists of highly trained analysts who work on defending and improving their organisation's defences around the clock. The blue team is expected to detect, oppose, and weaken the red team. The mock assault situation is outlined to upgrade their aptitudes by preparing for a real-world attack. The blue team will detect and neutralise more advanced assaults and closely monitor any current and imminent dangers to pre-emptively defend the organisation.
The Blue team objectives include:
- Understanding each stage of an incident and responding appropriately.
- Noticing suspicious traffic patterns and identifying indicators of compromise.
- Quickly closing any indicator of compromise.
- Identifying the red team/threat actors' command and control (C&C or C2) servers and blocking their connectivity to the target.
Undertaking analysis and forensic testing on diverse working frameworks their organisation's run, by utilizing third-party systems.Working alongside the red and blue teams, dissecting how they work together and prescribing any vital modifications to the current work out, or noting them for future reference.Seeing the big picture and accessing the mentality and obligations of both teams. For example, a purple team will collaborate with the blue team to audit how occasions are being identified. The team members at a certain point will move to the red team to address how the blue team's location capabilities can be subverted.
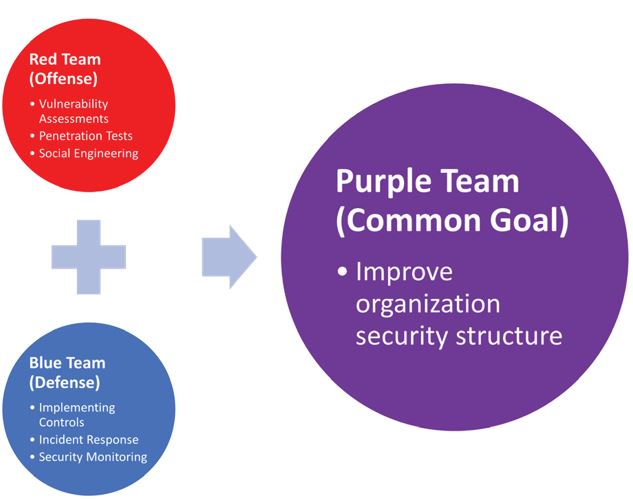
Impact of Purple team within an organization
The Purple team set up will benefit an organization. The team prepares and defends any threats that could leave an impact to the organization. For example, in some cases, a breach incident could take place by bypassing all defences, without having the blue team even noticing. This does not mean there is any lack in expertise or technology on the part of blue team, rather it demonstrates the complexity of an attacker's techniques and sophistication of their attack vectors. The purple team exists to eliminate such possibility. Red and blue teams work together and engage in a constant knowledge transfer to conduct simulation mimicking real life attack scenarios. The red team will help improve the organization's vulnerability management process, while the blue team helps in implementing controls, understanding attackers’ mindset, creating and developing a better incident response programs and vulnerability detection processes. The ultimate goal for both red and blue teams is to improve an organization’s security defences, in accordance with the organization’s goal which is to foster a better, more robust cyber security culture.
The primary incentive of a strong purple team is to regularly communicate between the offense and defence (blue and red teams). The Purple team provides a constant flow of information and a symbiotic work that could be done properly in organization. In addition, a purple team does not have to be a newly assembled team. It can function as an exercise between the two existing teams. The most crucial aspect is to empower communication and collaboration between team members, in order to advance the organization's cyber security culture consistently. One of the most important advantages of the purple team is that it can set up a viable security posture for the organization. Without the purple team’s constant communication, standard security reviews, new defence techniques, threat hunting, vulnerability management, and development of improved security infrastructure and policies, organizations would not stand a chance against malicious actors. After all, each team works together to help the organization better prepare for any future cyber threat.
Best practice of Purple team in an organization
If an organization is looking to improve current red team and blue team practices, with the implementation of a purple team, there are several factors which they need to consider. The organization needs to make sure that everyone understands their roles. Communication and collaboration are key because it is important for both teams to share their findings and help each other. They should never expect the red teams to engage in full vulnerability management process or to hold the blue team responsible as expert hackers. Establishing clear roles and expectations for each team, while keeping communication open goes far in ensuring a successful and effective purple team methodology. To realize the benefits from these exercises, it is important to plan well before executing the purple team exercises. Start the plan by defining goals, work on improving security alerts, security policies and processes. However, the plan need not be fixed. Continuously allowing adaptation might uncover any shortcomings which were never considered or planned during a threat-hunting demonstration. However, do set objectives and goals that are measurable. In this way, at the end of these exercises, their effectiveness can be easily assessed. Last but not least, before implementing these security remediations, make sure to revise and verify them. The team exercises need to be tracked at each and every step of the way, with every task assessed before moving on to the next step. Always follow up with actions. Reviewing each moderation continuously will help each side learn from each other, help close out any gaps, and permit for prioritized remediation rules. This will alleviate the red team with less monotonous shortcomings and direct the blue team towards uncovering more complicated threats.
Summary
The purple team exercise can help improve the viability of effectiveness in vulnerability detection, threat hunting and network monitoring by accurately simulating common threat scenarios to anticipate and distinguish evolving threats, technology and knowledge. Understanding and applying the concepts of purple teaming can benefit all organizations. A common mistake committed by organizations in adapting and assembling a purple team is not fully understanding its position and role to fit in along with red and blue teams, making the purple team exercise redundant and expensive, as opposed to providing higher value benefits if executed with proper conceptual understanding. Many organizations are already familiar with red and blue teams and have started to observe and realize some gaps from the exercises. Therefore, it can be concluded that purple teams is the missing piece to complete the cyber security puzzle within an organization.





